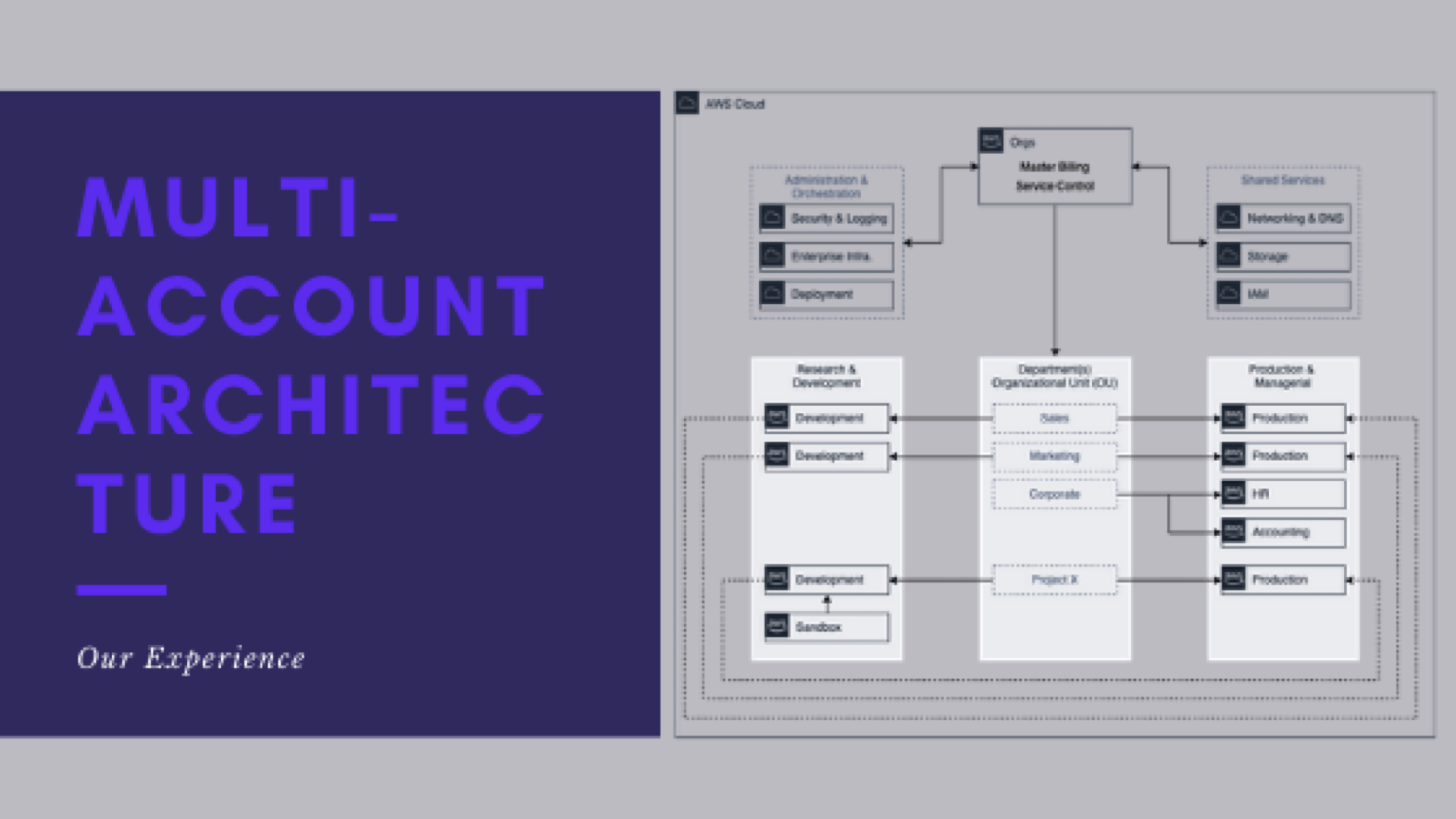
My experience with Multi-Account Architecture
/
0 Comments
This is post 2 of 9 in a multi-part series (hosted here) discussing…
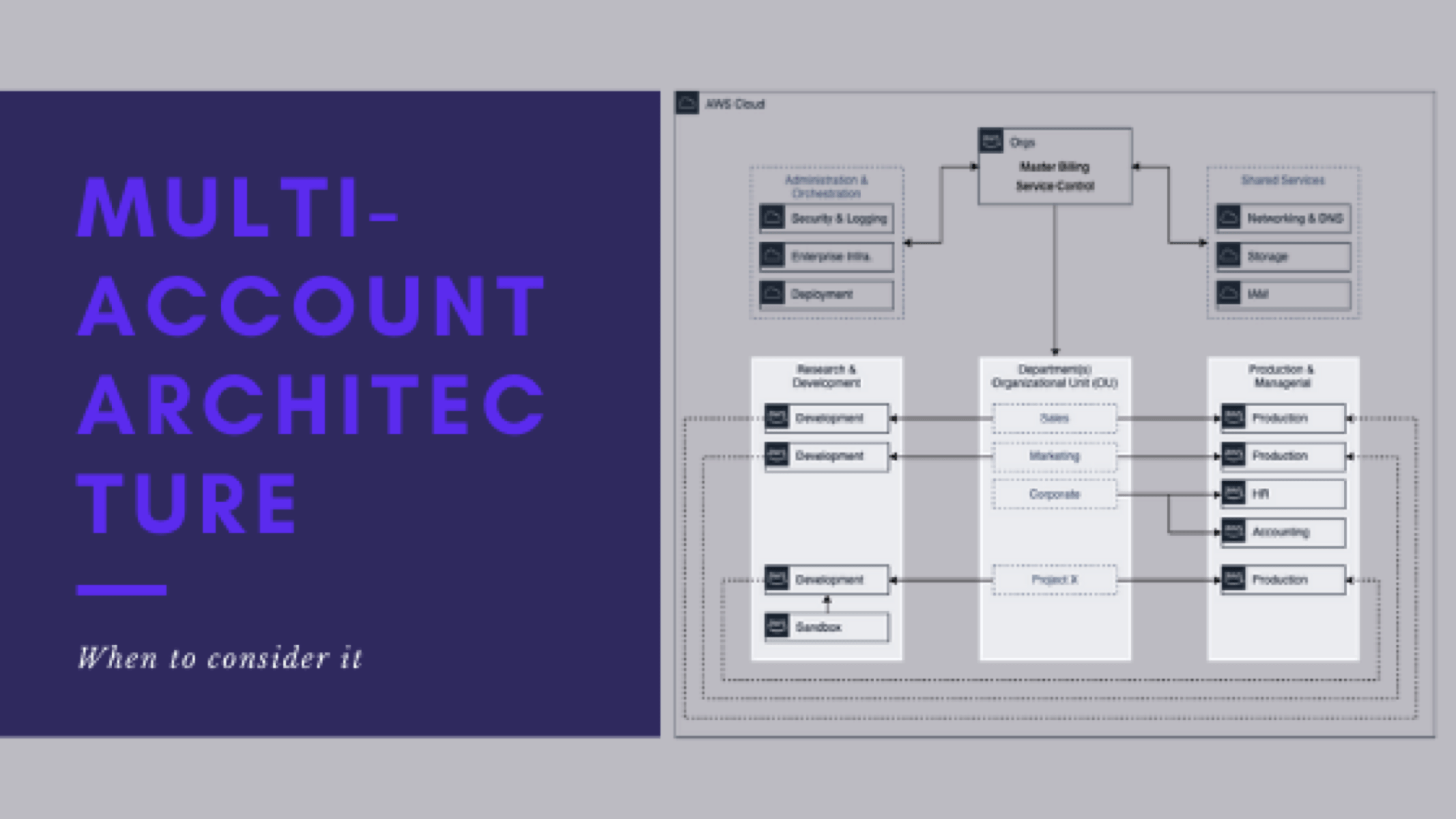
When to consider a multi-account architecture?
This is post 4 of 9 in a multi-part series (hosted here) discussing…
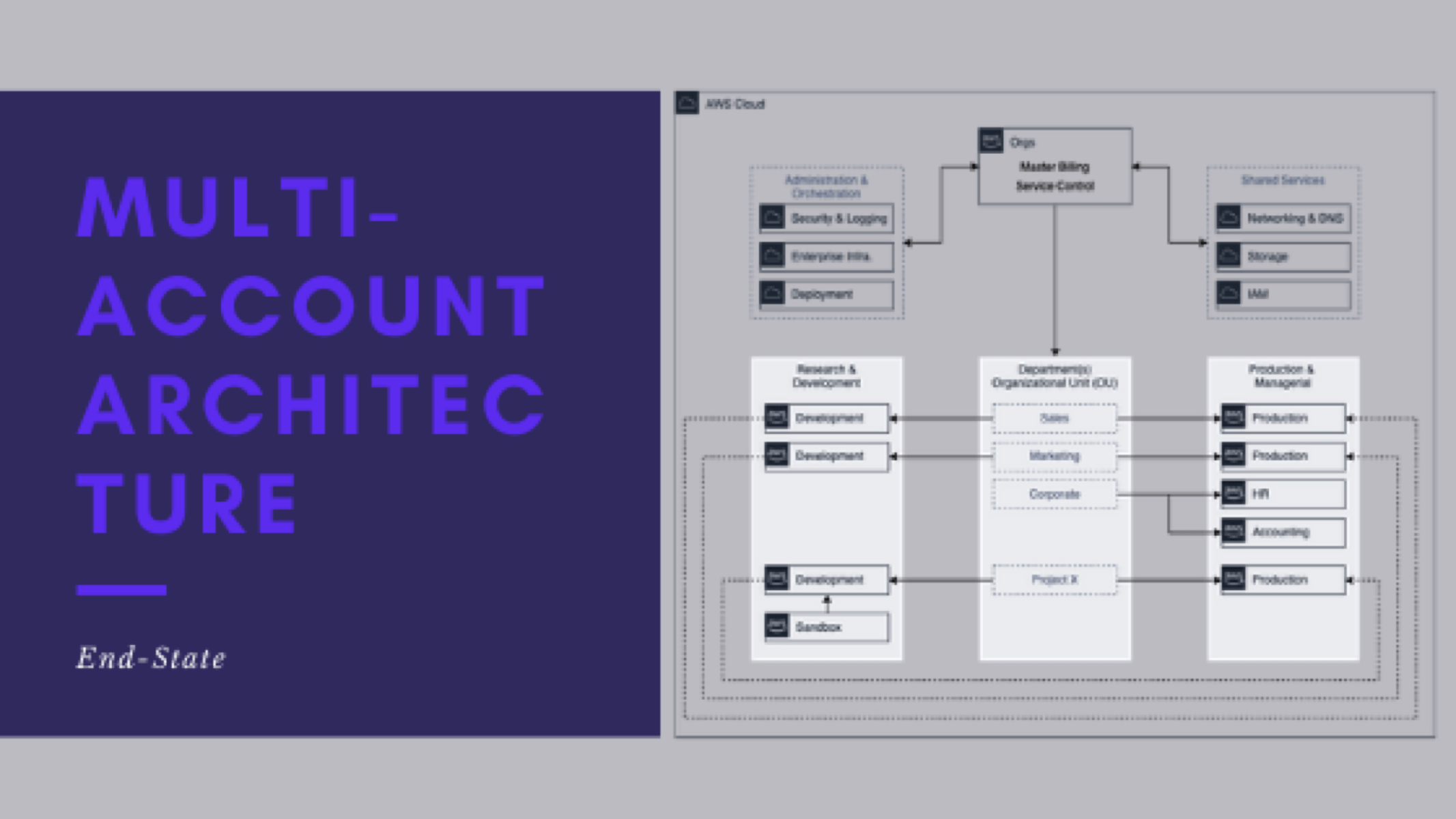
Multi-Account End-State
This is post 3 of 9 in a multi-part series (hosted here) discussing…
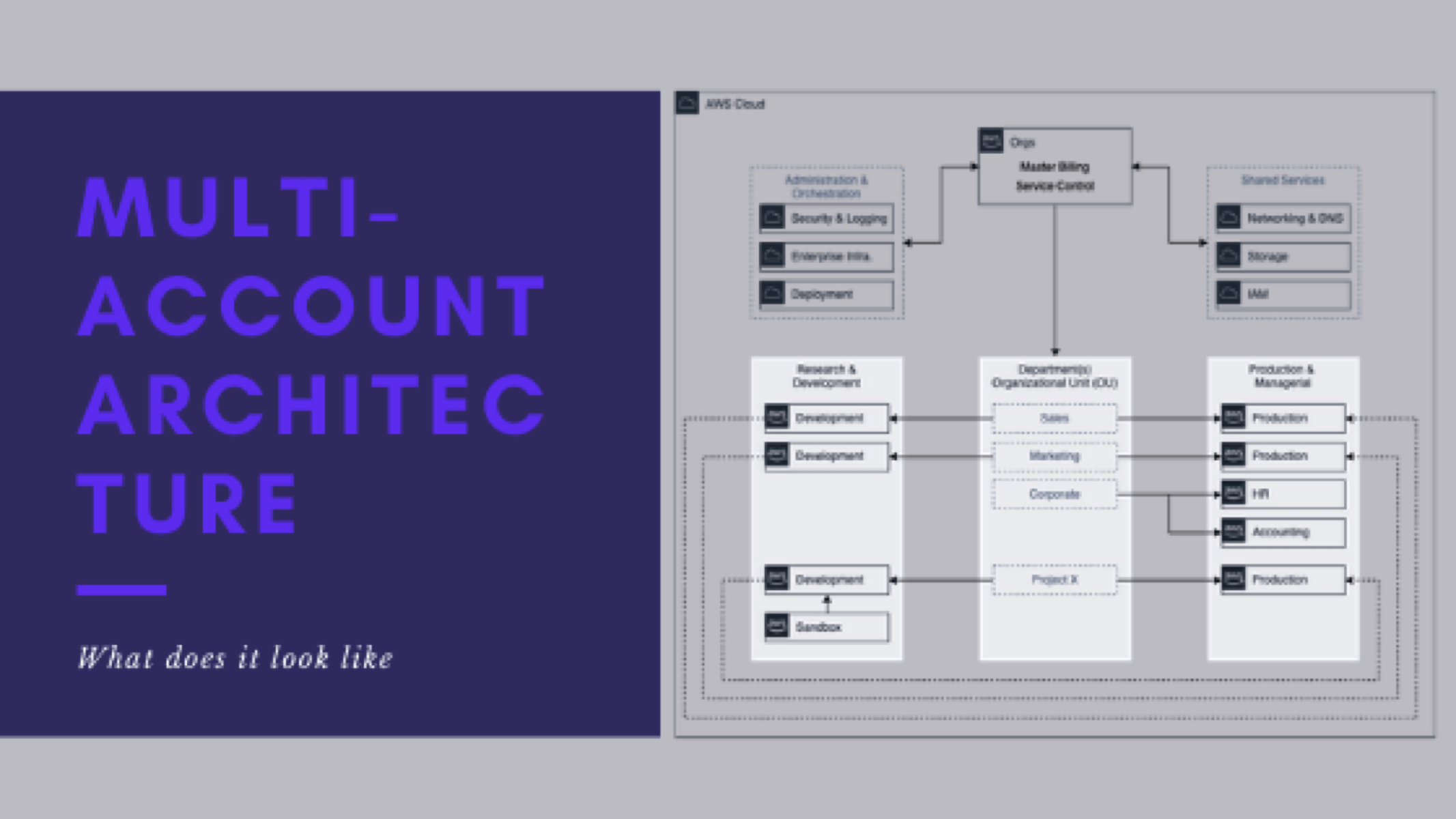
What a multi-account architecture might look like
This is post 6 of 9 in a multi-part series (hosted here) discussing…
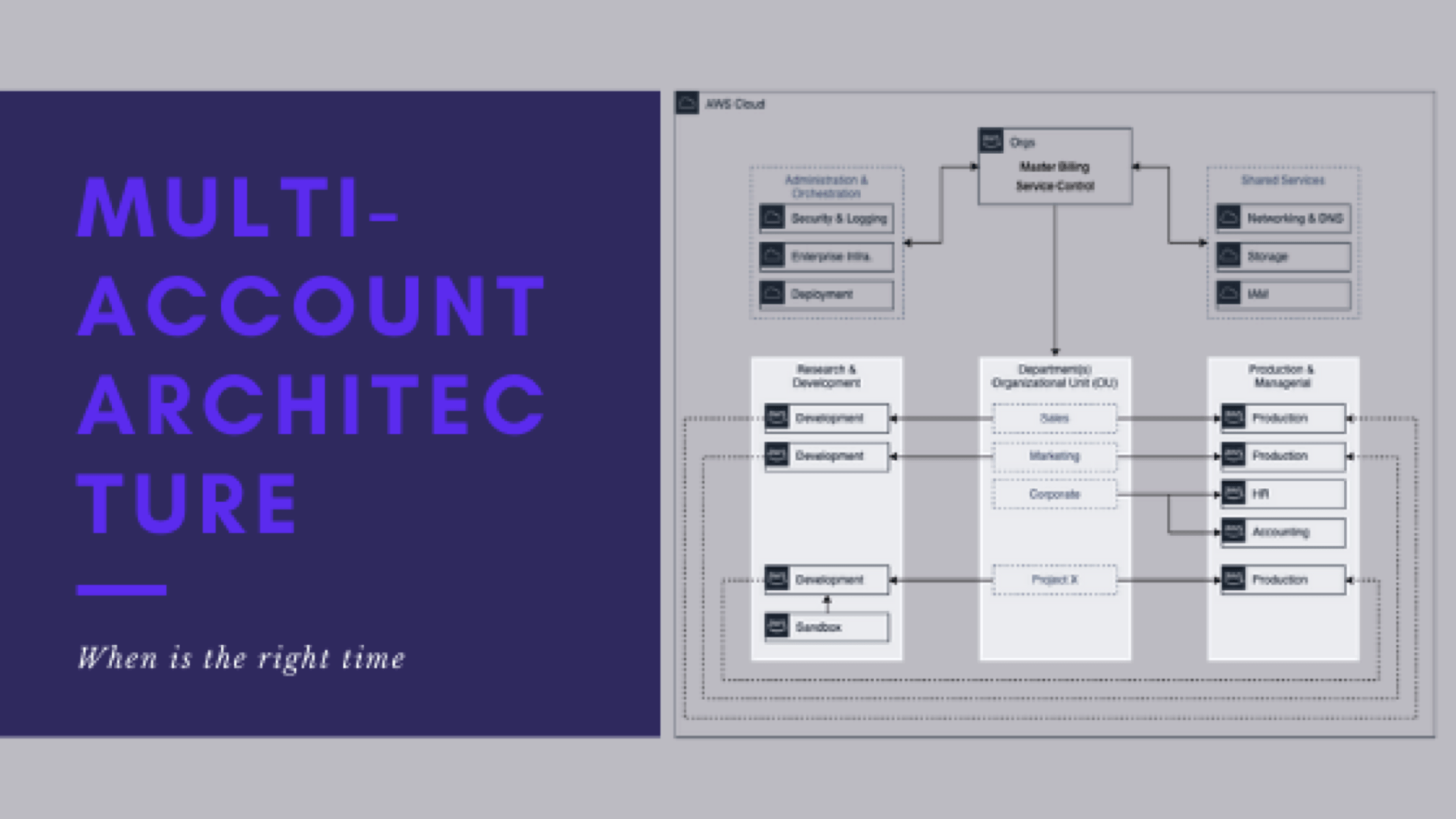
When is it right to implement a multi-account architecture
This is post 5 of 9 in a multi-part series (hosted here) discussing…
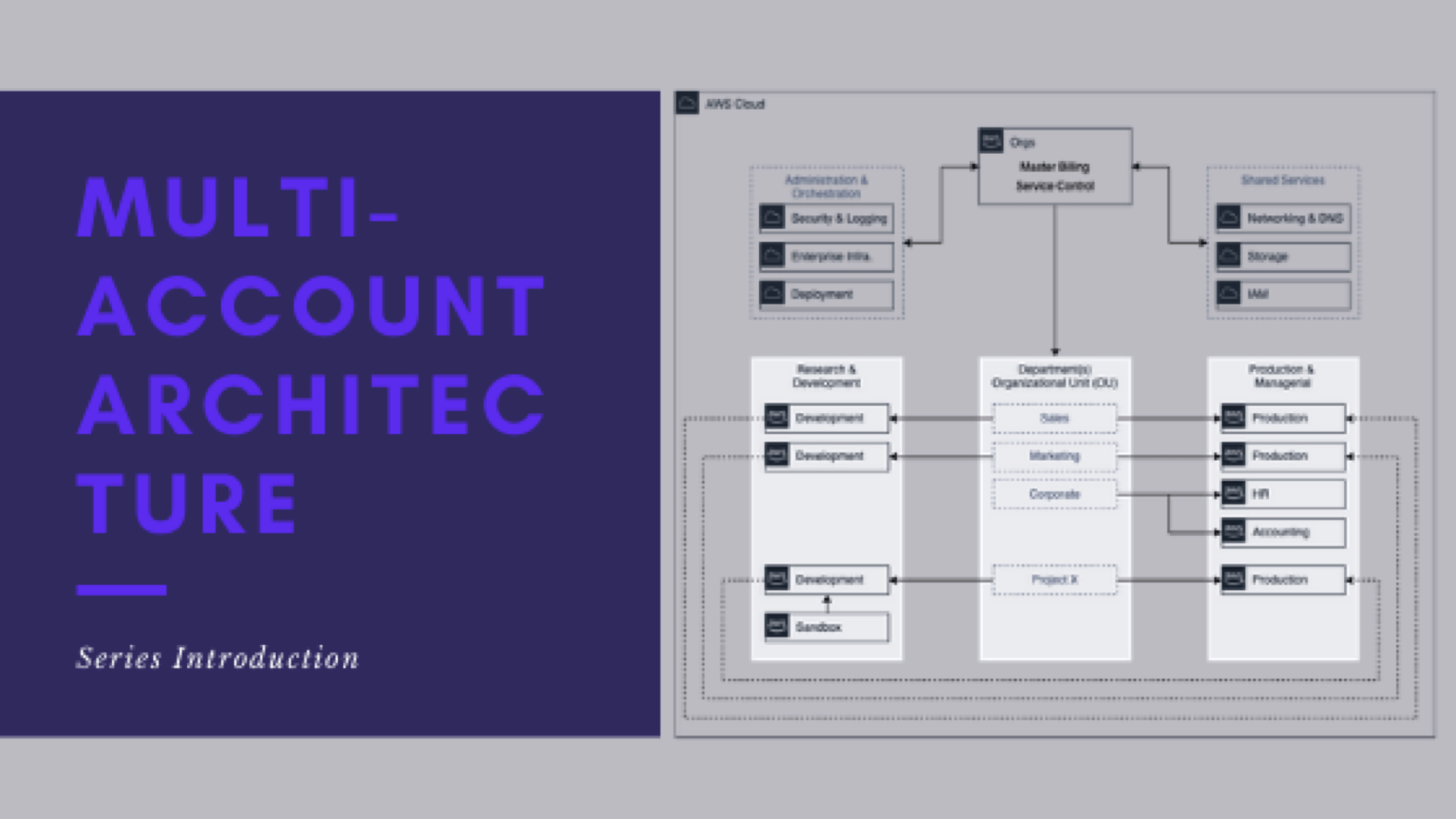
Multiple Cloud Account Architecture (Series)
This is post 1 of 9 in a multi-part series (hosted here) discussing…
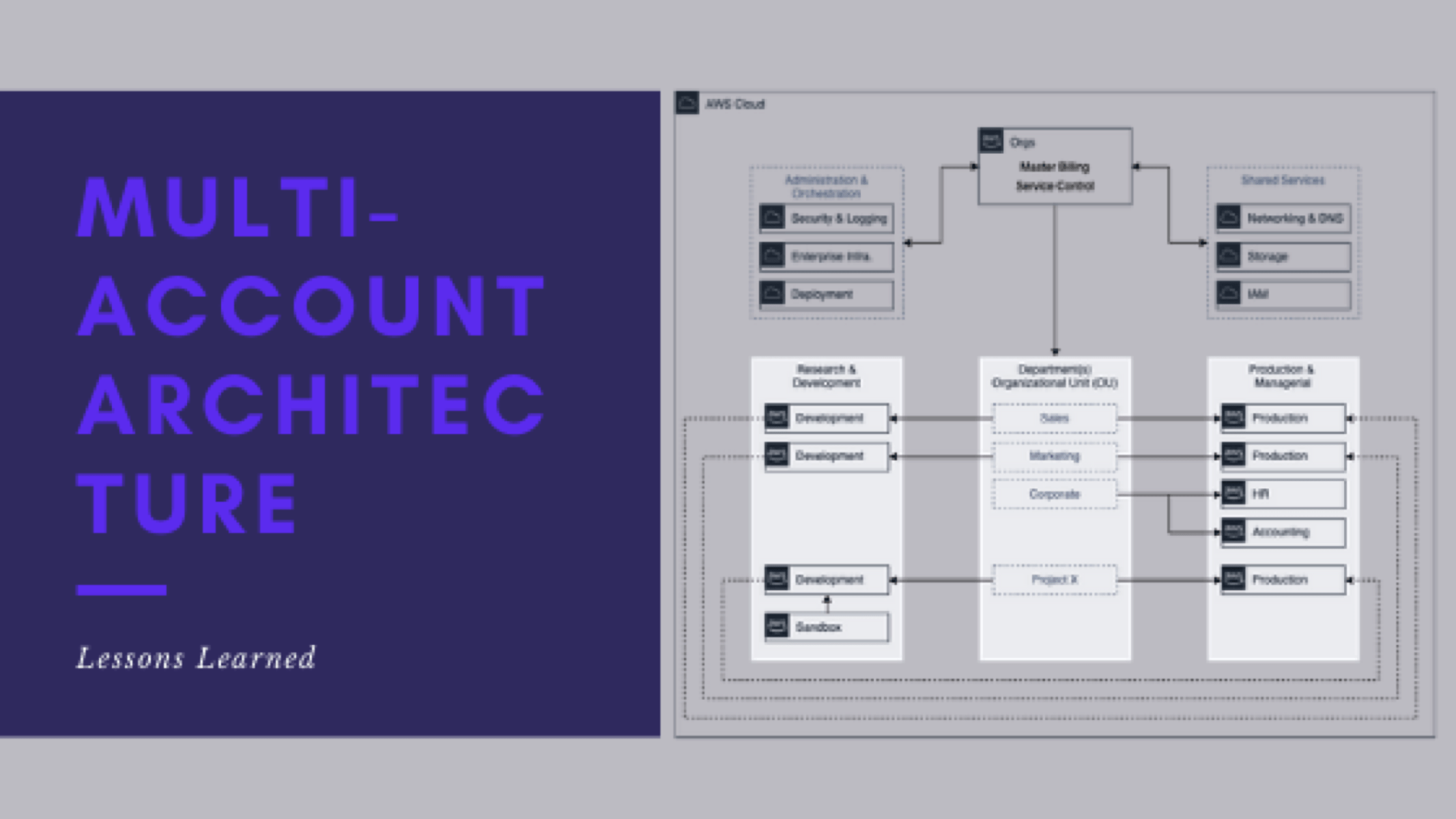
Lessons learned around multi-account architecture
This is post 9 of 9 in a multi-part series (hosted here) discussing…
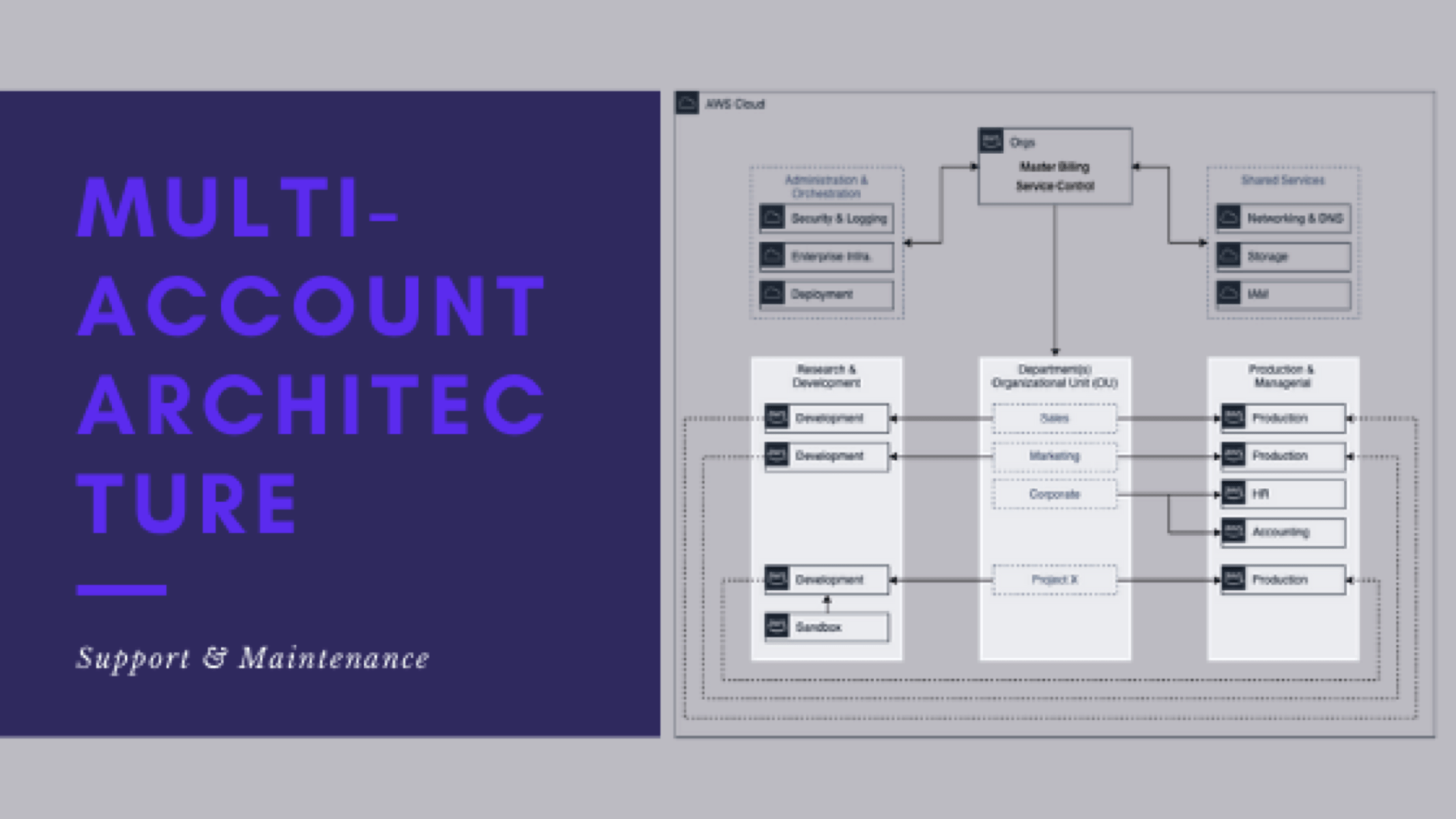
Support and maintenance of multi-account architecture
This is post 8 of 9 in a multi-part series (hosted here) discussing…
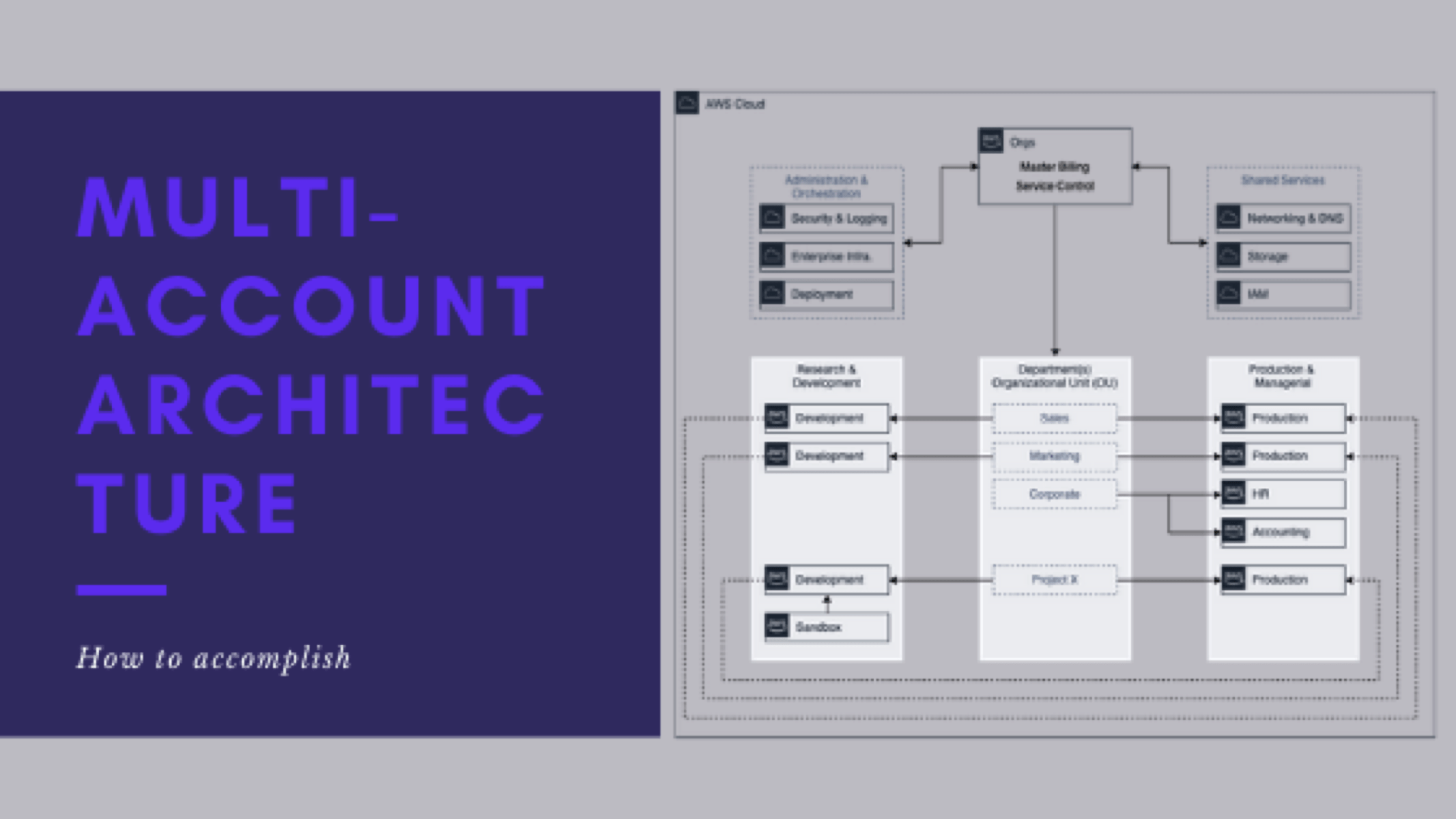
How to accomplish a successful multi-account architecture
This is post 7 of 9 in a multi-part series (hosted here) discussing…
